Setting Up SSO with OAuth
You can use OAuth protocol to integrate your identity provider like Okta with Y42 platform.
You can use OAuth protocol to integrate your identity provider like Okta with Y42 platform. The following explains how you can achieve that purpose:
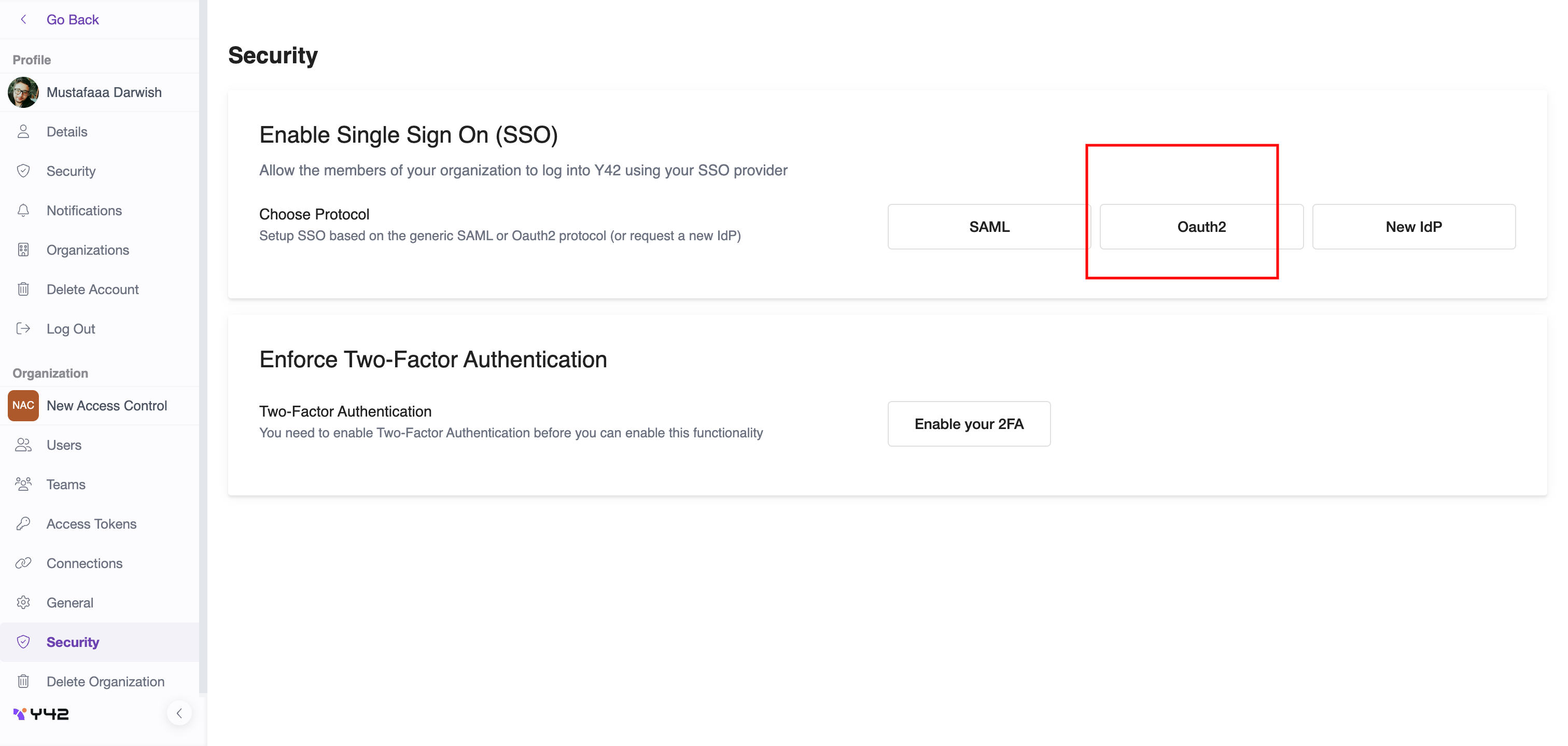
On that page click on OAuth2
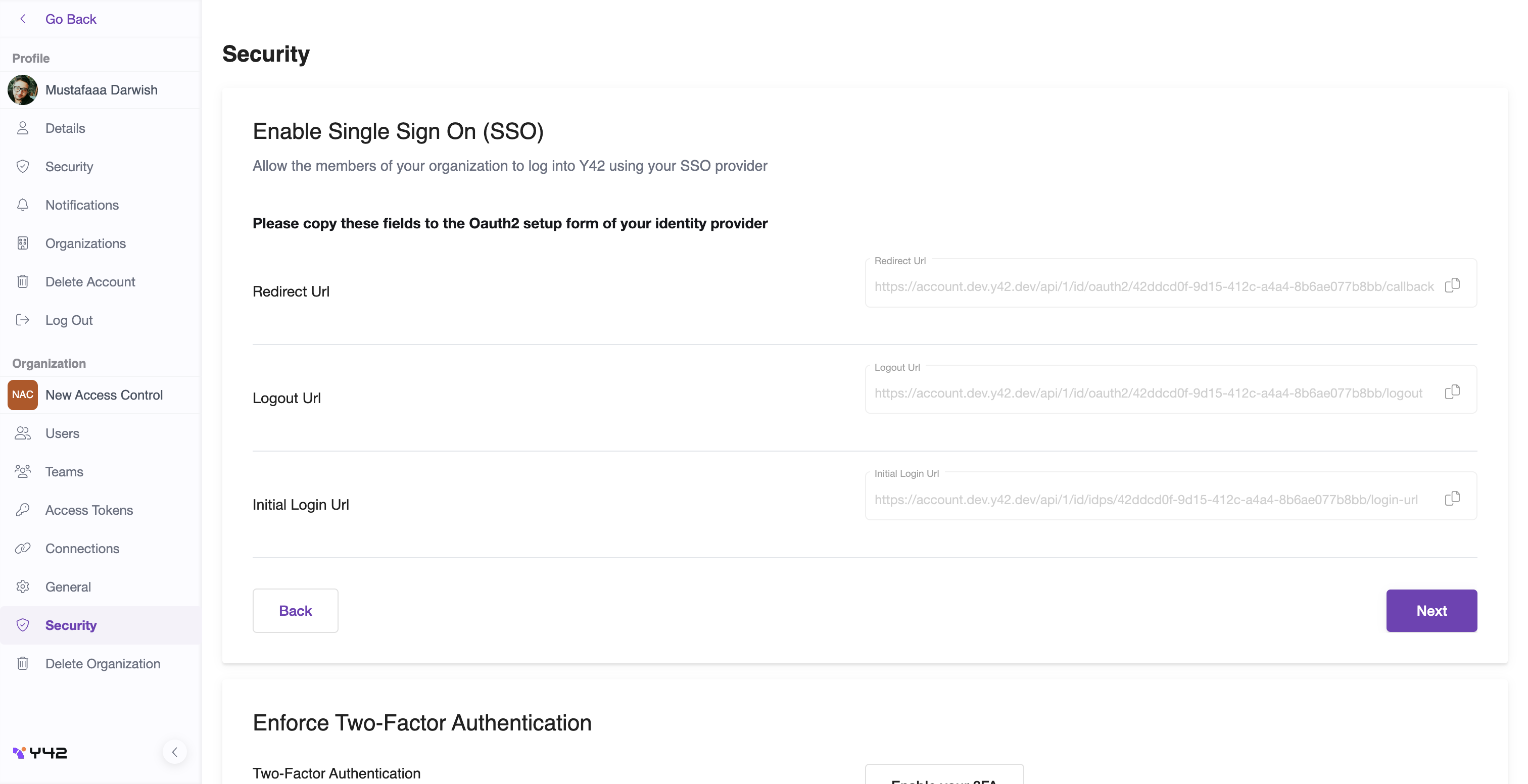
This page display 3 fields, the values for those field will be used in our identity provider, in that case we use OKTA, copy those value then go to Okta and select application and create new app as we done before in SAML, But this time we are going to choose Open
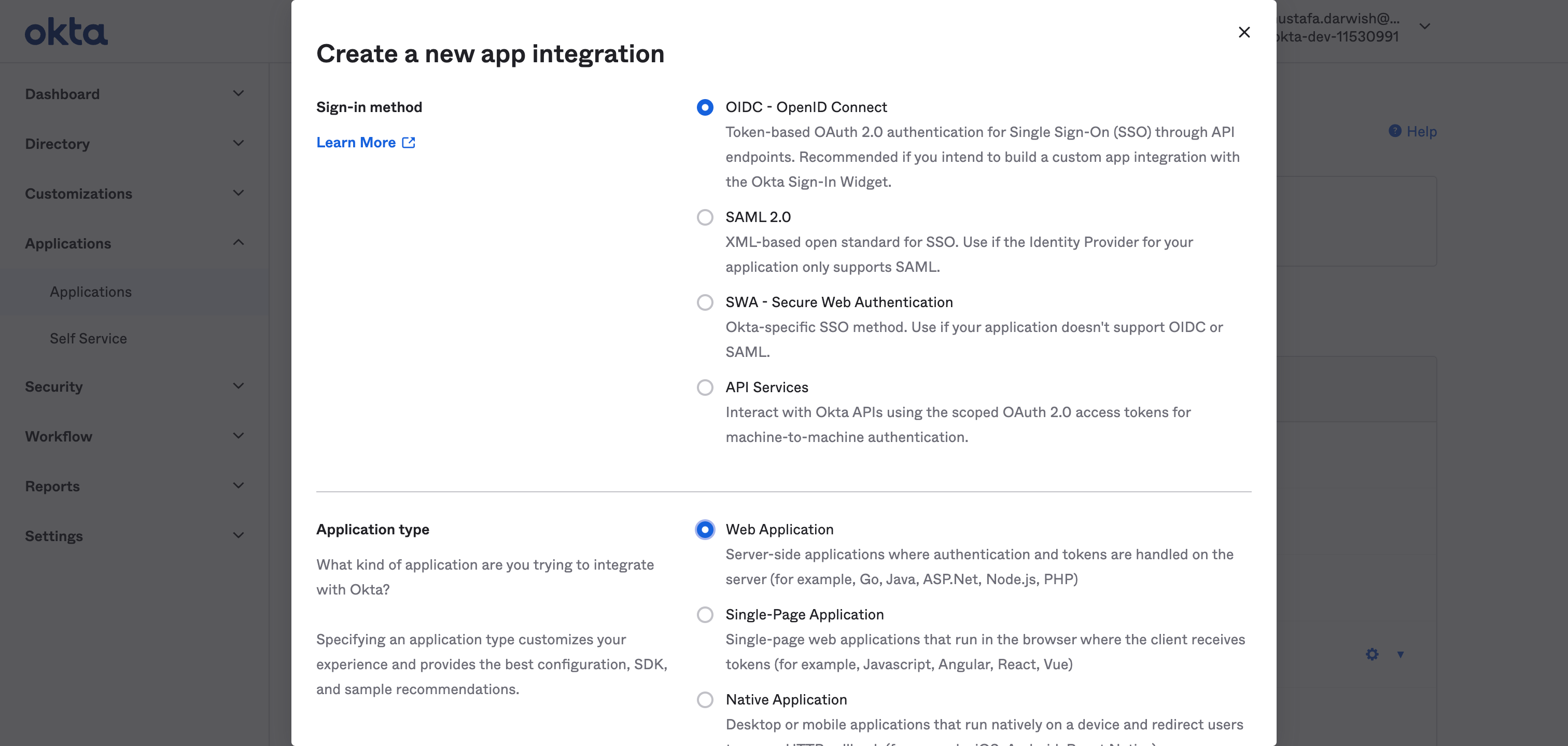
Selet OIDC - Open ID Connect and Web Application
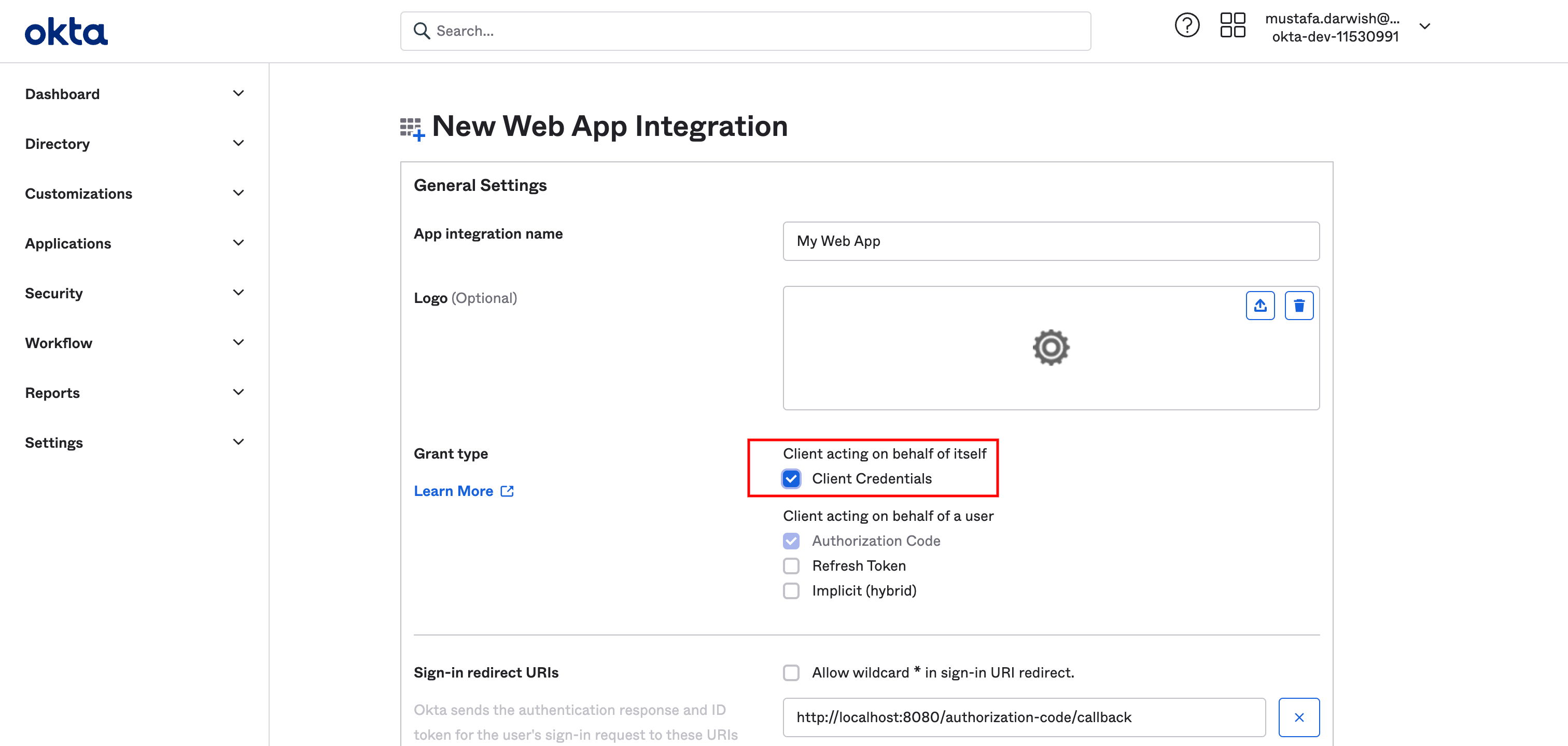
In that screen check client credentials option, scroll down
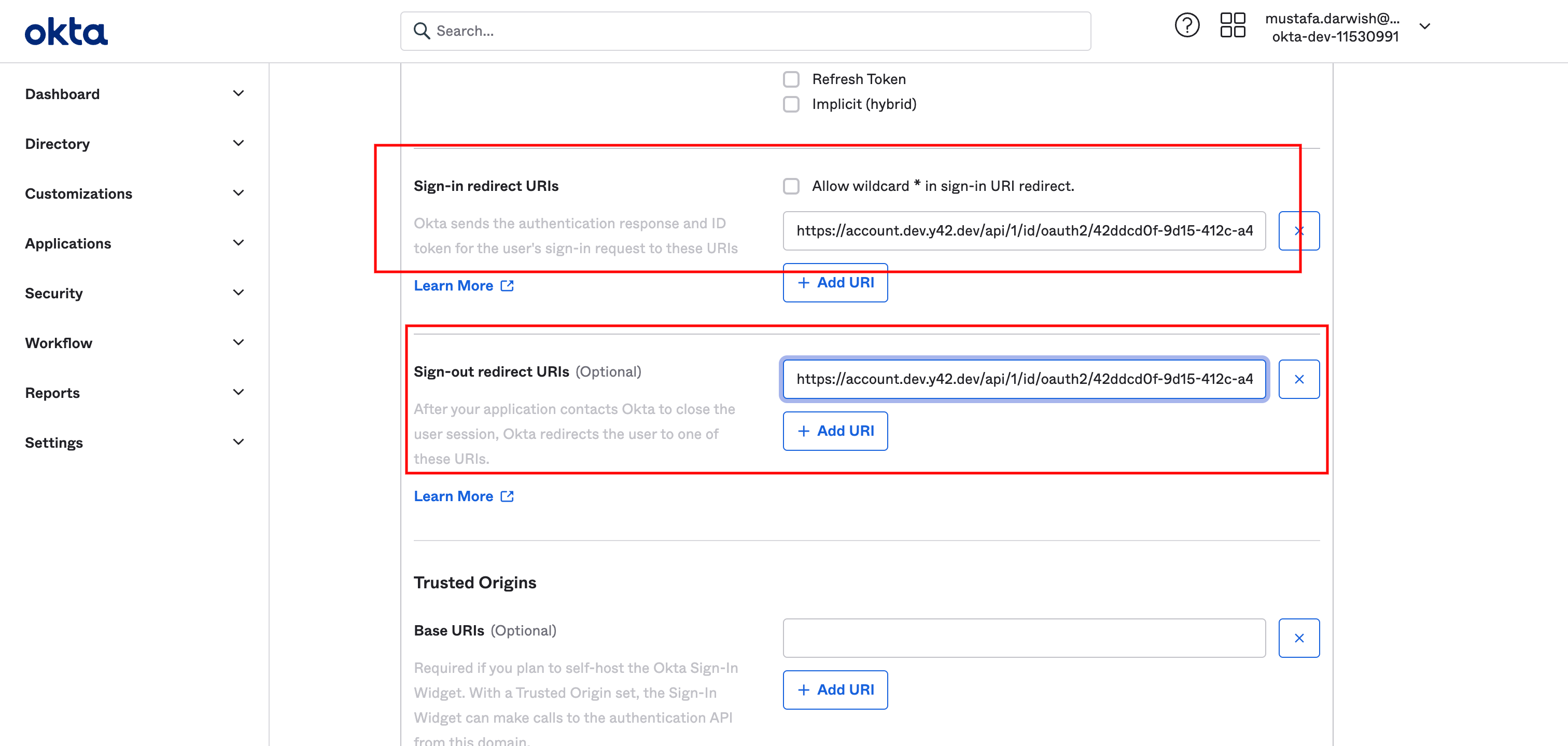
Fill in sign in url and sign out url with the corresponding values copied from Y42 settings screen. After that you can see the "Assignments" select it based on your needs. Click save and we are done setting on the Okta side
After saving you are going to see the following screen:
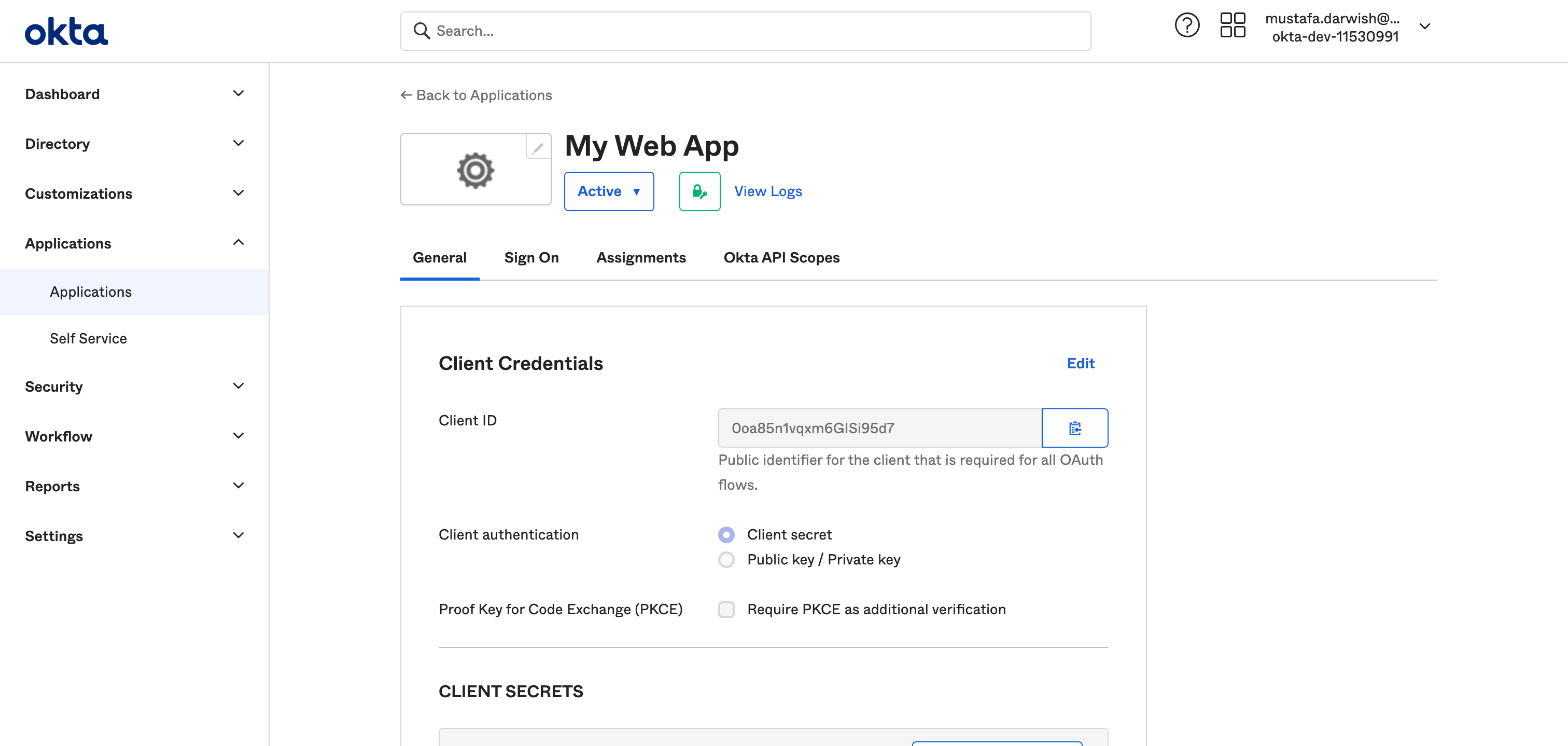
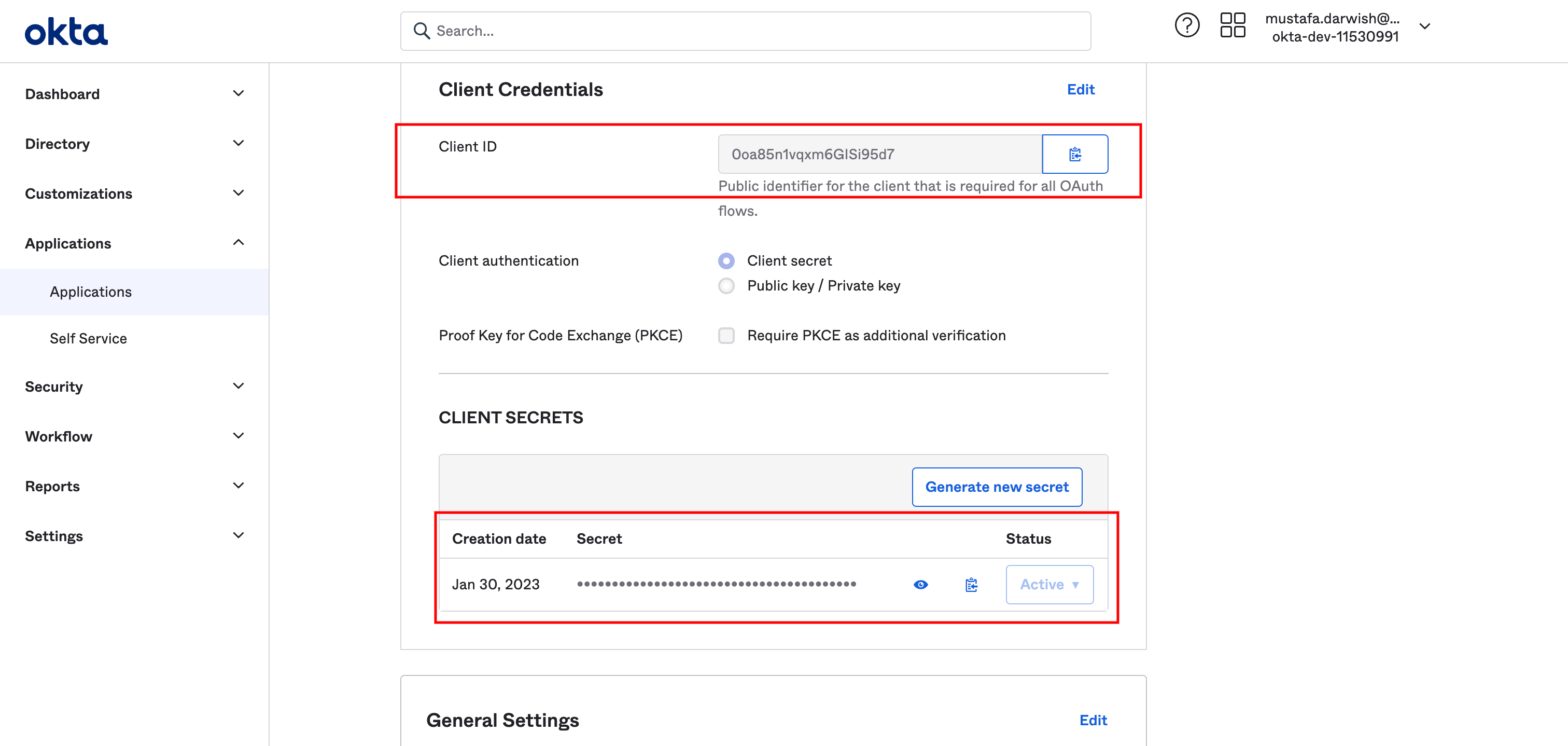
Copy the client id and secret as we are going to use them in Y42 settings
On the General section click edit
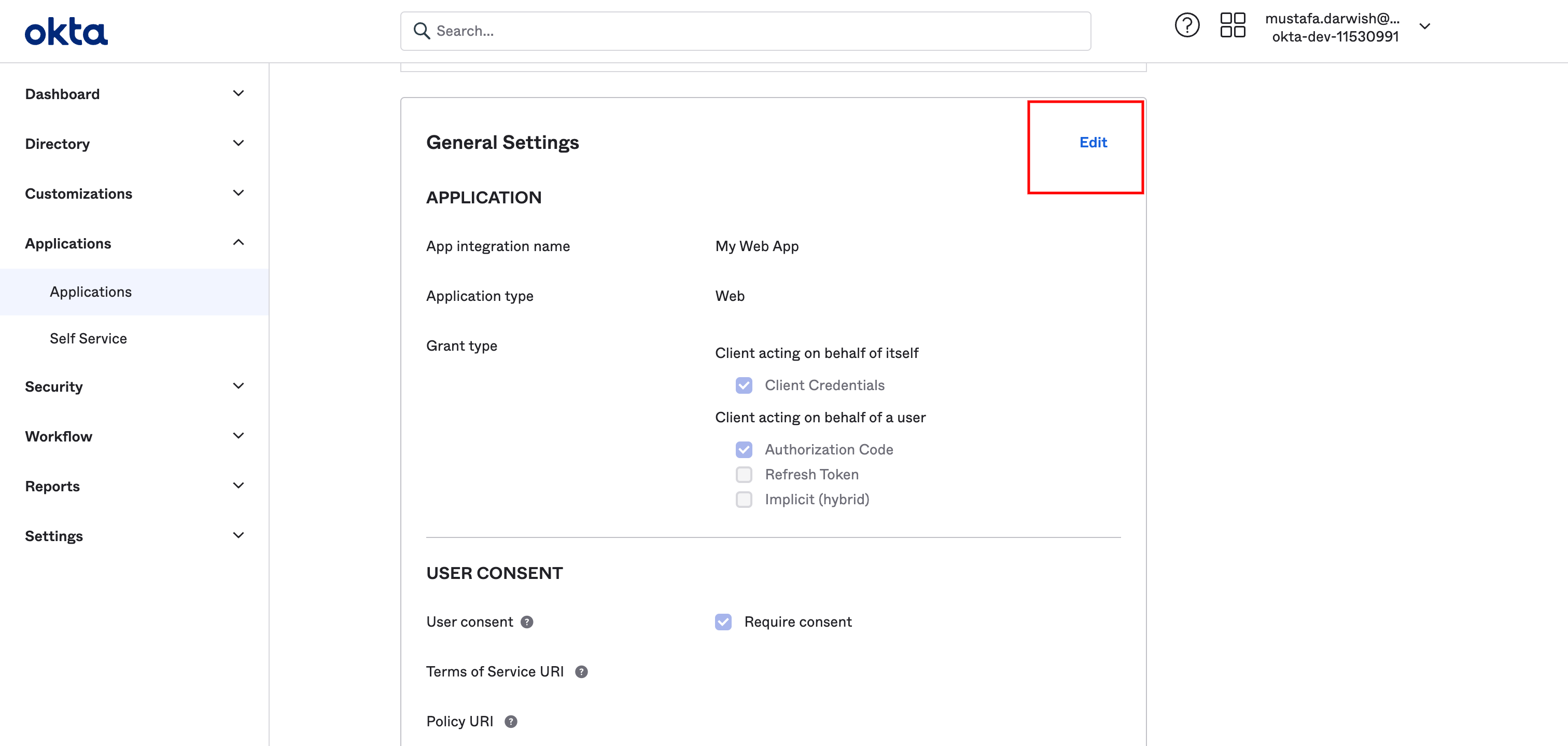
Then go to initial login url field and fill it with the corresponding value in Y42 settings
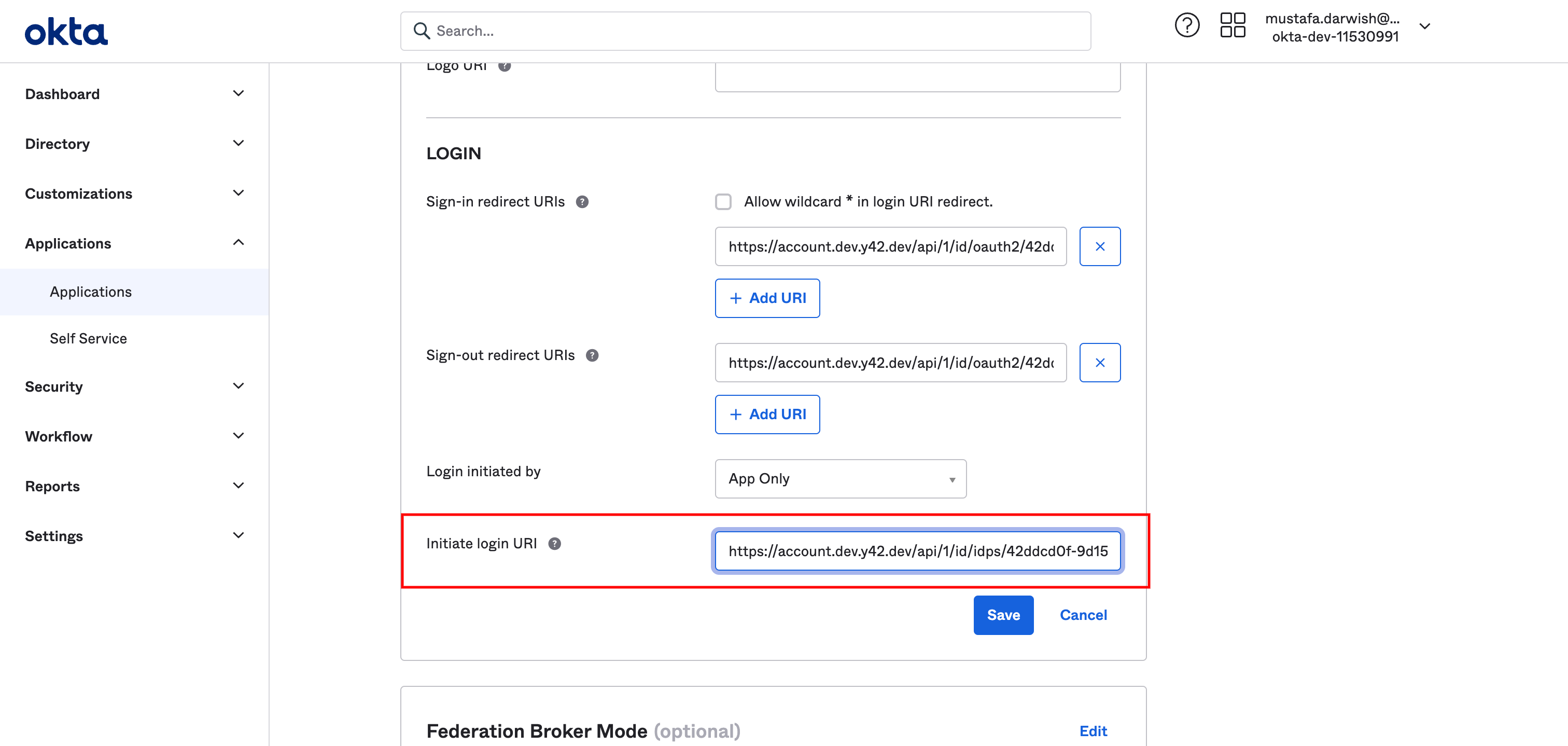
Then click save. Last thing, Copy the base url of OKTA in your address bar which is something like "https://dev-11530991-admin.okta.com/" and add that path to it's end ".well-known/openid-configuration" to be like https://dev-11530991-admin.okta.com/.well-known/openid-configuration. This url will serve as the SSO metadata URL used in Y42 settings later on.
Go to Y42 and then click on next. Fill in the name you want to your setting as well as the sso metadata url that we just mention above. once added you will notice the other fields are pre populated with values.
The only remaining 3 fields to enter are:
- Client Id → copied from okta
- Client secret → copied from okta
- Scope separator → enter a space " "
And click finish set up. Congrats, you've integrated Okta OAuth2 with your Y42 account
NOTES:-
- Any identity provider that support SAML or OAUTH2 can be integrated with our platform
- The metadata url for google is https://accounts.google.com/.well-known/openid-configuration
Updated almost 3 years ago